Understanding PCAP Files
Packet Capture, commonly referred to as PCAP, is a crucial file format in networking that allows for the storage of data extracted from network traffic.
This format plays a vital role in various applications such as network analysis, troubleshooting, and security assessments, offering deep insights into network behavior.
A PCAP file encompasses the complete raw data of network packets, which includes both headers and payload information, enabling a comprehensive review of all network communications.
To process these files, tools like Wireshark, TCPdump, and other monitoring software are frequently utilized. Once the data is captured, it can be scrutinized to resolve connectivity problems, assess network performance, or investigate potential security threats.
PCAP files provide a detailed perspective on network traffic, which is essential for recognizing patterns, spotting irregularities, and understanding the protocols in operation.
For network administrators, these files are instrumental in diagnosing complex issues, including packet loss, delays, or configuration errors. Security experts leverage PCAP files to probe into potential security threats such as malware attacks, unauthorized access attempts, or data breaches. By analyzing packet sequences, they can reconstruct sessions, trace unauthorized activities, and identify the source of attacks.
In essence, PCAP is an indispensable tool for anyone involved in network management or security, offering the visibility required to maintain efficient operations and protect against cyber threats.
PCAP files serve numerous purposes within network analysis and security operations. They empower network administrators, analysts, and researchers to scrutinize network traffic for several reasons:
-
Network Troubleshooting : These files assist in identifying network issues by analyzing packet-level details, including source and destination addresses, protocols, and error messages.
-
Network Security : PCAP files are essential for monitoring and investigating security incidents. They enable security professionals to examine packet contents, detect malicious activities, and follow the trail of network intrusions.
-
Protocol Analysis : The data in PCAP files provides extensive information about network protocols. By studying the captured packets, researchers can uncover insights into protocol behaviors, identify weaknesses, and devise strategies for mitigation.
-
Performance Monitoring : PCAP files can also be utilized to evaluate network performance, detect bottlenecks, and enhance network configurations. They offer a thorough view of network traffic, allowing administrators to analyze latency, throughput, and other critical performance indicators.
To effectively capture pcap files, utilizing a packet sniffer is essential.
A packet sniffer not only captures packets but also organizes them for easier comprehension.
The initial step in using a pcap sniffer is to determine the network interface for monitoring.
In a Linux environment, common interfaces include eth0 and wlan0.
The ifconfig command can help you identify and select the desired interface.
After choosing the interface, you can decide on the specific type of traffic to monitor.
For instance, if you are interested solely in tcp/ip packets, you can establish rules to focus on this traffic.
Numerous tools provide filtering options that enable you to manage the traffic you capture.
Wireshark, a popular packet analysis tool, offers both capture filters and display filters.
Capture filters allow you to control the packets that are captured, while display filters determine the packets shown to the user.
This functionality enables filtering by network protocols, specific flows, or particular hosts.
Once you gather the desired packets, you can analyze them for any performance issues.
For more precise analysis, filtering based on source and destination ports can help assess specific network components.
The data collected can be invaluable for troubleshooting network performance challenges.
There are various types of pcap files available, such as:
-
libpcap
-
winpcap
-
pcapng
-
npcap
Each format serves different purposes and is compatible with various network monitoring tools.
Libpcap is an open-source library targeted at Linux and Mac OS users, facilitating packet capturing and filtering.
It is commonly used by tools like tcpdump for packet processing.
For Windows users, winpcap serves as a similar portable packet capture library.
Winpcap also enables packet capturing and filtering but is no longer actively maintained.
Wireshark, nmap, and snort are some tools that utilize winpcap for device monitoring.
Pcapng, or the pcap next generation format, represents an advanced iteration of pcap.
It is the default format in Wireshark and supports both capturing and storing data.
Pcapng files can gather detailed information, including extended timestamp precision, user comments, and capture statistics, enhancing the user's analytical capabilities.
Packet Capturing Insights
Tools such as Wireshark utilize pcapng files due to their ability to capture more extensive information compared to traditional pcap files.
However, pcapng faces compatibility issues with numerous tools, limiting its widespread usability.
Npcap, developed by Nmap, is a versatile packet capturing library designed for Windows.
It offers improved speed and security over WinPcap, with features like support for Windows 10 and the capability for loopback packet capture injection, enabling users to both send and analyze loopback packets.
Moreover, Npcap is compatible with Wireshark.
One of the primary benefits of packet capturing is its ability to enhance network visibility.
Packet data can help identify the root causes of network issues, monitor traffic sources, and analyze the resource usage of various applications and devices.
Real-time information from pcap data is crucial for diagnosing and resolving performance issues, especially after a security incident.
For instance, tracking the flow of malicious traffic allows you to determine how malware infiltrated the network.
Without pcap and packet capture tools, monitoring packets and managing security threats becomes significantly more challenging.
Pcap’s simplicity as a file format is a notable strength, as it ensures compatibility with a wide range of packet sniffing applications across different operating systems, including Windows, Linux, and macOS.
This makes packet capturing adaptable to various environments.
Nonetheless, while packet capturing is an effective monitoring strategy, it does have its drawbacks.
Although it enables the observation of network traffic, it doesn't cover all angles.
Many cyberattacks may not traverse network traffic, necessitating additional security measures.
For example, certain attackers might employ USB drives and other hardware-based methods to compromise systems.
Thus, while pcap file analysis is a vital component of a comprehensive network security strategy, it should not serve as the sole defense mechanism.
Encryption poses another significant challenge for packet capturing.
Cyber attackers frequently use encrypted communications to execute their attacks, which can prevent packet sniffers from accessing critical traffic data.
As a result, encrypted attacks can go undetected if your approach is solely reliant on pcap.
The placement of the packet sniffer also affects its efficacy.
If positioned at the network's edge, the visibility for users may be restricted, potentially leading to missed detection of DDoS attacks or malware outbreaks.
Even when capturing data centrally, it's essential to ensure that comprehensive conversations are collected rather than just summary data.
Network Traffic Analysis Tools
Wireshark stands as the leading network traffic analyzer globally.
Utilizing .pcap files, it captures and logs packet data derived from network scans.
These packet files, identifiable by the .pcap extension, serve a critical function in diagnosing performance issues and detecting cyber threats within the network.
Essentially, a pcap file documents network activity, enabling you to analyze it using Wireshark.
This analysis allows for a thorough evaluation of the network's health and highlights any service-related problems that may require attention.
It's worth mentioning that Wireshark is not the sole option for opening .pcap files.
Other notable tools such as tcpdump and windump also provide the capability to analyze network performance using pcap files.
SolarWinds Network Performance Monitor serves as a powerful tool designed for comprehensive network monitoring, including the ability to capture PCAP data.
By installing this software on your devices, you can actively monitor packet data across your entire network.
This data is crucial for assessing network response times and identifying potential security threats.
Key aspects of the tool include:
-
Integration with WinPcap
-
Summary analysis of packet data
-
Protocol identification
-
Functionality for VoIP testing
-
Compatibility with Windows Server
Beyond PCAP viewing, SolarWinds Network Performance Monitor offers device status tracking, providing a robust suite of network management features with significant automation capabilities.
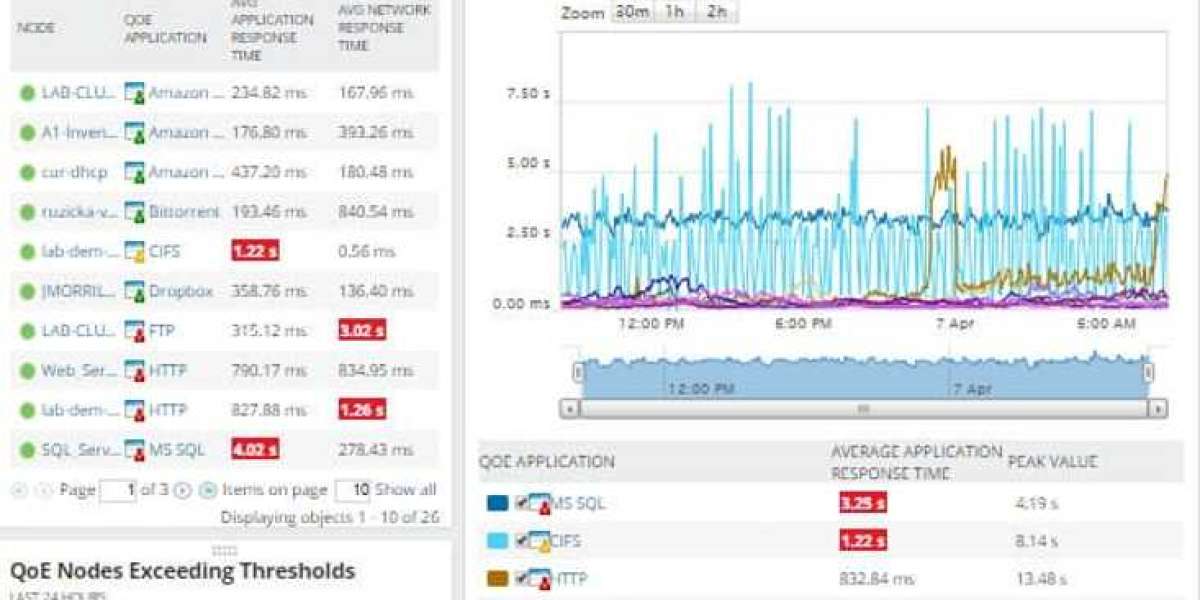
Users can analyze packet data via the Quality of Experience Dashboard , which presents a comprehensive overview of network performance.
Visual representations aid in detecting traffic spikes or suspicious activity that may suggest a cyber threat.
It's important to note that capturing and storing complete packets is not necessary for obtaining valuable insights from packet headers.
Flow protocols like NetFlow, IPFIX, sFlow, and j-flow can gather operational statistics from packet headers directly from network devices such as switches and routers.
This data can be accessed through the NetFlow Traffic Analyzer, which complements the Network Performance Monitor.
Together, these tools can be acquired as part of the Network Bandwidth Analyzer Pack.
For individuals primarily interested in packet capture and analysis, Wireshark may be a more suitable option.
However, for effective network management, a dedicated network monitor is essential.
The SolarWinds package is particularly beneficial for administrators of larger networks, offering both continuous monitoring and analytical capabilities.
Additional features include:
-
Presentation of packet data in lists and graphs
-
Header interpretation for summary statistics
-
Traffic analysis for popular applications
-
Reporting on average and maximum response times
-
Insights into Quality of Experience performance
-
Absence of raw packet display
The interface of the program allows users to distinguish applications based on their traffic loads.
Metrics like average network response time, average application response time, total data volume, and transaction counts keep users informed of real-time network changes.
A 30-day free trial of the software is also available for those interested in exploring its functionalities.
Packet Sniffing Overview
Packet sniffing is essential for any organization with a network infrastructure.
PCAP files serve as valuable tools for network administrators, allowing them to closely analyze performance and identify security breaches.
By capturing packets, organizations can not only pinpoint the root causes of attacks but also troubleshoot slow network performance.
There are several open-source packet capture tools available, such as Wireshark and Tcpdump, which enable network administrators to improve network efficiency without incurring high costs.
Additionally, proprietary tools exist for those seeking more sophisticated packet analysis capabilities.
With PCAP files, users can access a packet sniffer, gather traffic data, and assess where network resources are being utilized.
Applying the appropriate filters facilitates the process of filtering out irrelevant data, enabling a focus on critical information.
It's important to note that PCAP is not a subscription-based service. Most PCAP tools initiate packet capturing on an as-needed basis; however, capture sessions can also be automated through scripts.
A significant consideration with PCAP is the size of the files generated, as prolonged capture sessions lead to substantial amounts of data being stored.
The PCAP standard can express time with remarkable precision, down to nanoseconds—one billionth of a second.
All timestamps are calculated from an offset beginning January 1, 1970, at 00:00:00 UTC.
Libcap serves as an API, allowing other programs to control it.
It provides essential services for capturing network packets and is specifically designed for Unix and Unix-like systems, including Linux and macOS.
To effectively capture all network activity, the network interface card (NIC) must be set to "promiscuous mode," which disables the filter that typically limits the NIC to only reading packets addressed to it.
Libpcap, implemented in C, provides the PCAP functionality and consists of a library of function calls for other programs to utilize.
However, not all programming languages can directly invoke libpcap functions due to compatibility issues.
To bridge this gap, wrappers are created in language-native structures solely to call libpcap functions, translating data structures for compatibility.
It’s worth noting that the libpcap library does not include these wrappers.
In our market review of PCAP packet capture software, we evaluated various options based on specific criteria, including support for libpcap, WinPcap, PCAPNG, and Npcap.
Cross-Platform Packet Analysis Tools
-
Compatibility with Windows, macOS, and Linux systems
-
Management of packet storage files
-
Real-time graphical visualization of data
-
Tools for analyzing packets
-
Availability of a trial period for users to evaluate without cost or access to free tools
-
Options for free software or reasonably priced paid solutions
What is a Netflix VPN and How to Get One
A Netflix VPN is a virtual private network that enables users to access region-restricted content on Netflix by connecting to servers in different countries. By using a Netflix VPN, individuals can bypass geographical restrictions, allowing them to stream content exclusive to specific regions. To use a Netflix VPN, one must select a reliable VPN provider that supports streaming, set up an account, install the VPN software, and connect to a server in the chosen region to enjoy a wider array of Netflix programming.
Why Choose SafeShell as Your Netflix VPN?
If you're looking to access region-restricted content by using a Netflix VPN, you may want to consider the SafeShell VPN . One common issue with VPNs is that they fail to work because the software is outdated, which means they can't keep up with Netflix's detection mechanisms. SafeShell VPN, however, stands out with its high-speed servers specifically optimized for Netflix, ensuring you experience uninterrupted streaming with lightning-fast connection speeds. This allows you to enjoy buffer-free playback and high-definition content. Additionally, SafeShell VPN lets you connect up to five devices simultaneously, supporting a wide array of operating systems. This feature enables you to enjoy your favorite Netflix shows and movies on any device you prefer, regardless of the platform.
SafeShell VPN also offers an exclusive App Mode, allowing users to unlock and enjoy content from multiple regions at the same time, providing access to a wide variety of streaming services and libraries. The lightning-fast speeds guarantee that buffering and throttling are things of the past, offering unprecedented internet performance for streaming, downloading, and browsing. Moreover, SafeShell VPN ensures top-level security with its proprietary "ShellGuard" VPN protocol, which incorporates advanced encryption and robust security features, safeguarding your data from prying eyes. So, if your Netflix VPN is not working as expected, switching to SafeShell VPN could be the solution for secure and unrestricted entertainment access.
A Step-by-Step Guide to Watch Netflix with SafeShell VPN
To enjoy Netflix content from various regions using SafeShell Netflix VPN , follow these simple steps:
-
Subscribe to SafeShell VPN by visiting their website, selecting a suitable plan, and clicking the "Subscribe Now" button.
-
Download and install SafeShell VPN by choosing your device and downloading the appropriate app or software version from the website.
-
Launch the SafeShell VPN app, log in to your account, and select the APP mode for optimized Netflix streaming.
-
Choose your VPN server by browsing the list of available servers, selecting one in the desired region, and clicking "Connect" to establish a connection.
-
Finally, open the Netflix app or website, log in with your account, and enjoy the content available in the region you selected.